Transport Layer Security
TLS helps ensure that most web-based encrypted communication cannot be easily decrypted using just the server’s private key, because only a portion of the session key actually gets transmitted through the network. In addition, the session key is periodically renewed between client and server. Because of this, all the session keys would be needed to decrypt traffic in the event of a private-key compromise. The latest version (1.3) of TLS also contains only cipher suites that support Forward Secrecy.
Record Protocol
- All TLS packets are sent using the record protocol
- This header is attached to every single message
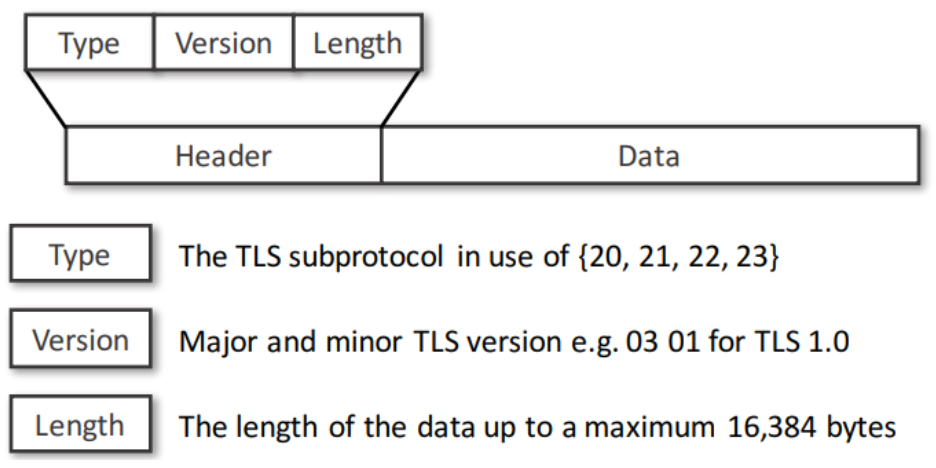
- The type: which kind of TLS message is sent (1 byte)
- 20 ChangeCipherSpec
- The sender has sufficient information and is switching to encryption or to a new cipher suite
- It is a single message that is sent very rarely
- By starting encryption for the first time, it is saying that the handshake has been successful, and encryption can start
- The sender has sufficient information and is switching to encryption or to a new cipher suite
- 21 Alert
- An SSL-level alert notification (example close_notify). not necessarily an error.
- Example: problem with the handshake, received data length is wrong, warning.
- An SSL-level alert notification (example close_notify). not necessarily an error.
- 22 Handshake
- Messages sent right at the beginning (example ServerKeyExchange)
- To establish a cipher, to establish our keys
- Messages sent right at the beginning (example ServerKeyExchange)
- 23 Application Data
- Opaque application data.
- Any applications data once we start the encryption is going to be sent under protocol 23
- 20 ChangeCipherSpec
- The version: which TLS version is used (2 bytes)
- 03 01 TLS 1.0 = SSL 3.1
- 03 02 TLS 1.1
- 03 03 TLS 1.2
- 03 04 TLS 1.3
- The length: how long is the payload of the message (2 bytes)
- The data field depends on the type of message
Requirements
The TLS handshake protocol is used to establish parameters for the remainder of the session.
It must:
- Agree ciphers and protocols
- Authenticate the server (and client)
- By default, only the Server is Authenticated, the Client is NOT.
- Establish shared secrets
- Be robust to tampering and attack
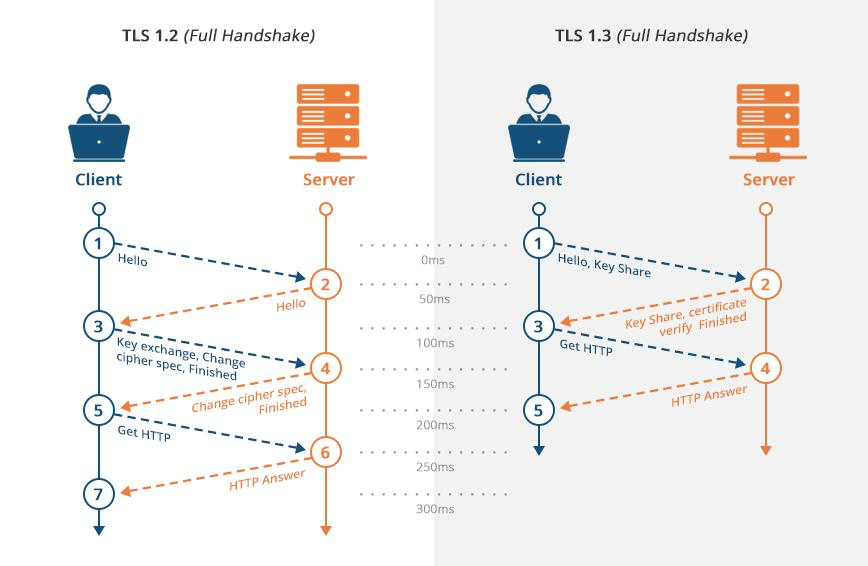
Handshake
For a Byte by Byte explanation, have a look at:
- TLS 1.2: https://tls12.xargs.org
- TLS 1.3: https://tls13.xargs.org
History
-
SSL and TLS are protocols for internet handshakes and encrypted transmission
- Secure Socket Layer (SSL) came first, then after v3.0 it became Transport Layer Security (TLS), currently v1.3
- People still use SSL as a term, even though technically it’s now TLS
-
It is the primary mechanism for encryption for HTTP communication, that is called HTTPS
- But it is perfectly usable to encrypt communication over the internet with other protocol than HTTP.
-
TLS working group created in 1996 between Netscape and Microsoft
- 1999: SSL renamed TLS 1.0 (minor changes to SSL 3). TLS 1.0 is equivalent to SSL 3.1
-
Over time, extensions added to TLS 1.0
- To add backward-compatible plugin bits into the handshake to allow sending additional information
-
TLS 1.1 mostly didn’t change the protocol.
- It added security fixes and removed some methods of encryption
-
TLS 1.2 is a more flexible protocol, lots of TLS extension, the hashing function has been improved
- It introduces authenticated encryption, which is the most modern form of encryption
-
TLS 1.3 released in August 2018
- The protocol has been redesigned to make it faster
- A lot of the old ciphers have been removed to make it more secure.
- TLS 1.3 only supports authenticated encryption (AEAD)
- Most server/devices offer TLS 1.3
- But most servers still support TLS 1.2 for legacy reasons
Relevant Note(s):