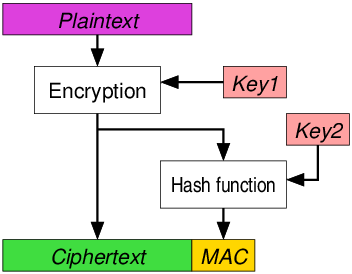
Authenticated Encryption
- Enables one-step construction from an Insecure to a Secure Channel
- Authenticated Encryption is a “one-step” cryptographic primitive that simultaneously handles authentication & encryption.
- Authenticated Encryption with Associated Data (AEAD)
- Provides Authenticity and Confidentiality
- Authenticity: Ensures the message was created by the holder of the secret key and has not been altered by a single bit. If a message is tampered with, the decryption process will return a
FAILerror rather than corrupt data. - Confidentiality: Ensures the payload (plaintext) is secret and unreadable to eavesdroppers.
- Authenticity: Ensures the message was created by the holder of the secret key and has not been altered by a single bit. If a message is tampered with, the decryption process will return a
- What is “Associated Data”?
- AD refers to data that needs to remain visible (unencrypted) but must be tamper-proof.
- Example:
- In a network packet, the IP header (destination address) must be visible, so routers know where to send it.
- However, you want to ensure an attacker hasn’t changed the destination IP.
- AEAD protects the integrity of this header (Associated Data) while encrypting the packet body (Payload).
- Provides Authenticity and Confidentiality
- Implementation Examples
Relevant Note(s):